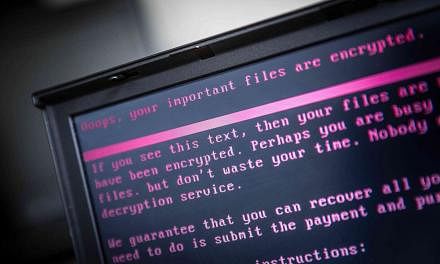
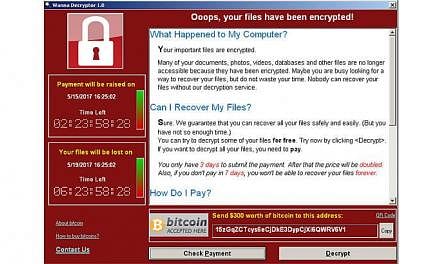
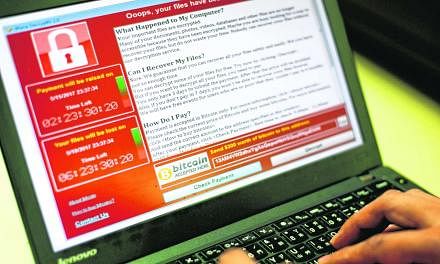
SINGAPORE/TORONTO • Technical staff are scrambling to patch computers and restore infected ones, amid fears that the ransomware worm that stopped car factories, hospitals, shops and schools last Friday could wreak fresh havoc today when employees log back on.
"At the moment, we are in the face of an escalating threat. The numbers are going up - I am worried about how the numbers will continue to grow when people go to work and turn (on) their machines on Monday morning," Europol director Rob Wainwright told Britain's ITV.
Today is expected to be a busy day, especially in Asia, which may not have seen the worst of the impact yet.
"Expect to hear a lot more about this tomorrow morning when users are back in their offices and might fall for phishing e-mails" or other as yet unconfirmed ways the worm may propagate, said Singapore- based security researcher Christian Karam.
In Singapore, a company that supplies digital signage, MediaOnline, was rushing to fix its systems after a technician's error led to 12 kiosks being infected in Tiong Bahru Plaza and White Sands.
Director Dennis So said the systems were not connected to the malls or tenants' networks.
Mr Marin Ivezic, a Hong Kong- based cyber security partner at PwC, said some clients have been "working around the clock since the story broke" to restore systems and install software updates or patches, or restore systems from back-ups.
Microsoft released patches last month and last Friday to fix a vulnerability that allowed the worm to spread across networks.
But new versions of the worm - dubbed WannaCry ransomware - are expected, said cyber security experts, and the extent of the damage from last Friday's attack remains unclear. The latest count is over 200,000 victims in at least 150 countries.
Code for exploiting a cyber weapon called "Eternal Blue" was released on the Internet in March by a hacking group known as the Shadow Brokers. It claimed the bug was stolen from a repository of National Security Agency hacking tools. The US agency has not responded to requests for comment.
The malware hit Britain's National Health Service particularly hard, causing widespread disruptions and interrupting medical procedures across hospitals in England and Scotland.
When asked if the British government had paid any ransom in this situation, a Downing Street spokesman said last Saturday that it had not.
"Usually, ransomware attacks are designed to be revenue sources but, in this case, the ransom was quite low," Europol spokesman Jan Op Gen Oorth said.
In Germany, Deutsche Bahn faced "technical disruptions" with electronic displays at train stations, but travel was unaffected.
Other targets in Europe included Spanish telecom giant Telefonica, French car maker Renault and a local authority in Sweden, which said that about 70 computers had been infected.
In Asia, some hospitals, schools, universities and other institutions were affected. China National Petroleum Corporation petrol stations could accept only cash payments after the company's computer system came under attack, reported Shanghai-based Thepaper.cn.
A Jakarta hospital said yesterday that the cyber virus had infected 400 computers, disrupting the registration of patients and the finding of records.
Last Saturday, a cyber security researcher tweeting as MalwareTechBlog helped to limit the spread of the virus by registering a domain name used by the malware.
"Essentially, they relied on a domain not being registered and, by registering it, we stopped their malware spreading," @MalwareTechBlog told Agence France-Presse in a private message on Twitter.
REUTERS, WASHINGTON POST, AGENCE FRANCE-PRESSE