Comparing NotPetya and WannaCry and tips on how to stay safe from ransomware
Sign up now: Get ST's newsletters delivered to your inbox
SINGAPORE - The latest ransomware identified as NotPetya that hit the Windows computers of businesses, port operators and governments is said to be more dangerous and intrusive than WannaCry, which spread in May (2017).
Here's a look at how the two ransomware stack up:
1. Both use the 'phishing' method
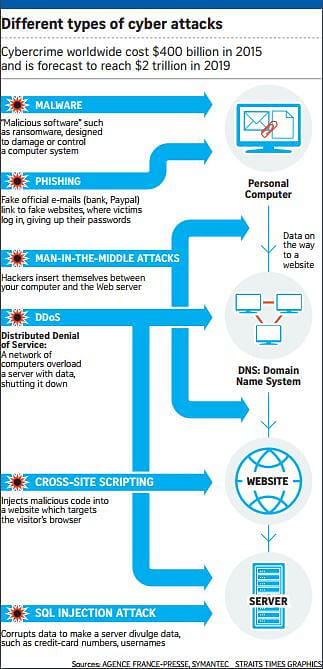
NotPetya and WannaCry infect computers using a method known as "phishing" to get unsuspecting e-mail users to click on booby-trapped attached Office documents. The documents, once opened, will download and run the WannaCry or NotPetya installer and push the worm to spread to other connected computers. Infected systems are locked down with a note demanding a ransom.
2. Both infect through Eternal Blue
United States-based security software firm Symantec confirmed that NotPetya was infecting computers through at least one system vulnerability known as Eternal Blue. Eternal Blue, a hacking tool used by the National Security Agency, was leaked online in April (2017) by a group of hackers known as the Shadow Brokers. The same vulnerability was used in May to spread WannaCry, which infected hundreds of thousands of computers in more than 150 countries.
3. No kill switch for NotPetya yet
An accidental move by a 22-year-old researcher in Britain, identified as "MalwareTech", activated the kill switch for WannaCry and halted its spread within days. But there is no kill switch found for NotPetya, Mr Beau Woods, deputy director of the Cyber Statecraft Initiative at the Atlantic Council in Washington, reportedly said.
4. NotPetya unleashes greater damage than WannaCry
The Singapore Computer Emergency Response Team (SingCert) described NotPetya as "more dangerous and intrusive" than WannaCry. Unlike WannaCry which encrypts a computer's files, NotPetya encrypts a segment of the hard drive that renders the entire computer inoperable. NotPetya also reboots the infected machine to display the ransom message, according to United States-based security software maker Forcepoint.
What can organisations do to limit the damage and stay safe?
a. Patch systems immediately
The patch has been available from Microsoft since earlier this year (2017). Check out https://technet.microsoft.com/en-us/library/security/ms17-010.aspx. According to SingCert, vulnerable systems include:
•Windows 10
•Windows RT 8.1
•Windows 8.1
•Windows 7
•Windows XP
•Windows Vista
•Windows Server 2016
•Windows Server 2012 and Window Server 2012 R2
•Window Server 2008 and Windows Server 2008 R2
b. Do not pay the ransom
Mr Nick Fitzgerald, security software maker ESET Asia-Pacific's senior research fellow, said that paying is no longer possible as the e-mail to send the bitcoin wallet ID and "personal installation key" has been shut down along with the infection. "People shouldn't pay for the ransom as they will not be able to receive the decryption key," he said.
c. Back up important files
Critical files must be backed up daily, and the copies should be kept offline, according to security experts. Backed-up copies of critical files should also be encrypted. Computer users are also advised not to click on e-mail attachments from unknown sources.


