SEOUL • Cyber security researchers have found evidence that they say could link North Korea with the massive cyber attack that began last Friday.
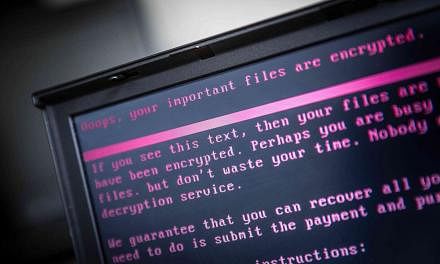
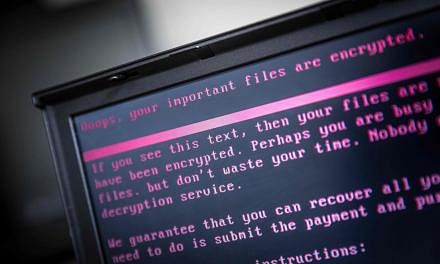
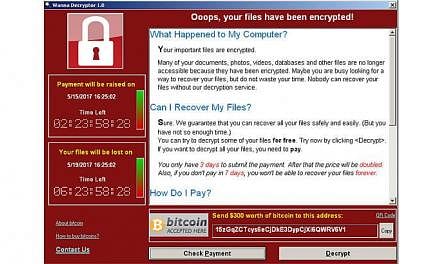
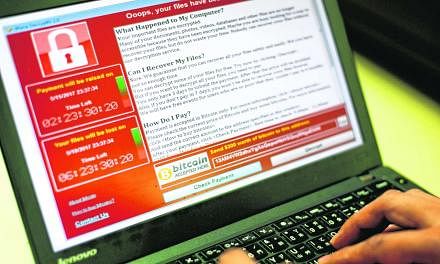
The WannaCry ransomware has so far infected more than 300,000 computers worldwide.
Singapore's Cyber Security Agency (CSA) said last night that computers tied to some 500 Internet protocol addresses or Internet accounts could have been infected, but that their files might not be encrypted.
The Pyongyang link emerged when a researcher from South Korea's Hauri Labs said yesterday that its own findings matched those of Symantec and Kaspersky Lab, which said on Monday that some code in an earlier version of the WannaCry software had also appeared in programs used by the Lazarus Group, believed to be a North Korea-run hacking operation.
"It is similar to North Korea's backdoor malicious codes,"said Mr Simon Choi, a senior researcher with Hauri who has done extensive research into North Korea's hacking capabilities. He said he "saw signs last year" that the North was preparing ransomware attacks.
Both Symantec and Kaspersky said it was too early to tell whether North Korea was involved in the attack, based on the evidence that was published on Twitter by Google security researcher Neel Mehta.
Europe's cross-border police agency Europol also warned against a rush to judgment.
-
Lazarus linked to other high-profile hacking cases
-
The Lazarus Group, acting for impoverished North Korea, has been more brazen in its pursuit of financial gain than others.
About two months ago, cyber security company Symantec said it was likely that Lazarus was behind a recent cyber campaign targeting organisations in 31 countries.
Researchers have uncovered four pieces of digital evidence suggesting that the Lazarus Group was behind the campaign that sought to infect victims with "loader" software used to stage attacks by installing other malicious programs, Symantec said in a blog.
"We are reasonably certain" that Lazarus was responsible, Symantec researcher Eric Chien said at the time, according to a Reuters report.
In February last year, cyber security firms said Lazarus was behind the theft of US$81 million (S$113 million) from the central bank of Bangladesh. In that heist, the hackers stole the money from an account that Bangladesh held with the Federal Reserve Bank of New York and transferred it electronically to accounts in the Philippines.
The most high-profile hacking was in November 2014, when Sony Pictures Entertainment's network was crippled for weeks. Embarrassing e-mail messages and personal details about movie stars were exposed. It was believed to be in retaliation for Sony's release of The Interview, a political satire about a fictional plot to kill North Korean leader Kim Jong Un.
Sony initially withdrew the film but eventually released it on Christmas Day that year.
REUTERS
Threatening more cyber chaos, a group that claimed to have leaked cyber spying tools belonging to the United States National Security Agency, including those used in the WannaCry attack, said it would release more tools.
The Shadow Brokers, a group with possible links to Russia, said it would begin releasing tools on a monthly basis to anyone willing to pay for access to some of the tech world's biggest commercial secrets.
Last Friday's ransomware attack, which slowed on Monday, is among the fastest-spreading extortion campaigns on record.
In China, Foreign Ministry spokesman Hua Chunying said she had no information to share, when asked about the origin of the attack and a possible North Korea link.
Several Asian countries have been affected by the malware, although the impact has not been as widespread as some had feared.
In Malaysia, cyber security firm LE Global Services said it had identified 12 cases so far, including a large government-linked corporation, a government-linked investment firm and an insurance company.
It did not name any of the entities affected.
"We may not see the real picture yet, as companies are not mandated to disclose security breaches to the authorities in Malaysia," said LE Global chief executive Fong Choong Fook. "The real situation may be serious."
In Singapore, the CSA's Singapore Computer Emergency Response Team said it received some calls asking about ransomware prevention and patching but none asking for help to recover from the ransomware. Those seeking help can do so via e-mail at singcert@csa.gov.sg or by calling 6323-5052.
Taiwan Power said that nearly 800 of its computers were affected, although these were used for administration, not for systems involved in electricity generation.
More attacks were possible, Mr Choi said, "especially given that unlike missile or nuclear tests, they can deny their involvement in attacks in cyberspace and get away with it".
REUTERS, AGENCE FRANCE-PRESSE