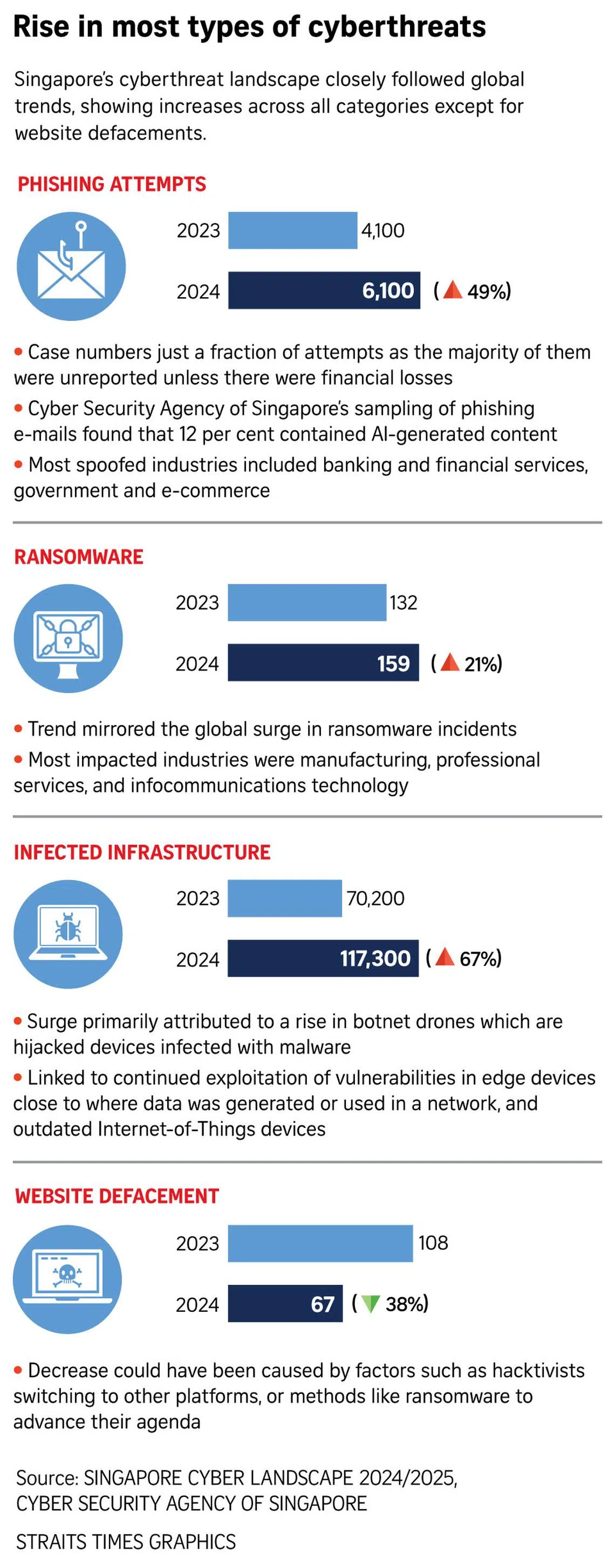
Failure to patch vulnerable software sees malware infections in Singapore surge 67% in 2024: CSA
Sign up now: Get ST's newsletters delivered to your inbox

The report said Singapore ranked as the third-largest source of distributed denial-of-service attack traffic.
PHOTO: REUTERS
SINGAPORE – The number of systems here infected by malware in 2024 leapt to 117,300 – a 67 per cent spike from about 70,200 in 2023 – with most incidents occurring because users failed to update vulnerable software.
Advanced persistent threat (APT) actors
The ninth edition of the annual Singapore Cyber Landscape report, published on Sept 3 by the Cyber Security Agency of Singapore (CSA), attributed the surge of infected systems to a rise in infected botnet drones.
Botnet drones are computers, servers or Internet of Things devices that malware has taken over, allowing a botnet operator to control them remotely.
Threat actors could have accessed such devices by exploiting vulnerabilities in network edge devices like routers, web cameras or smart TVs.
CSA said its analysis revealed that most of the infections involved old malware strains with readily available remediation measures that had not been adopted.
“This underscored a troubling fact – that even as ransomware and other cyber threats grew, users were still failing to update and patch vulnerable software,” said the agency.
Initiatives to address this gap include Singapore’s participation in an international operation against a global botnet in September 2024 that disabled malware from 2,700 devices locally.
The CSA report also noted that APT activity has increased around the world, and in South-east Asia, such activity primarily targeted government and critical infrastructure for espionage purposes.
“State-sponsored groups have focused on targeting network edge devices and using relay networks to blend in with existing network traffic to limit detection and complicate attribution,” the report said. Relay networks are networks of computers or devices that pass data from one point to another, often to mask the origin of the traffic or improve delivery efficiency.
The report highlighted some prominent incidents linked to APTs, such as attacks by a group called TAG-43, whose victims include Asean government organisations, a Cambodian political party, and a non-profit democracy-focused organisation.
For Singapore, it was previously reported that the number of suspected APT attacks in the country increased more than fourfold from 2021 to 2024.
The report also noted that the Republic has been a target for APT groups, most recently UNC3886
To defend against these highly sophisticated state actors, CSA works more closely with critical infrastructure owners and their suppliers, and runs large-scale cyber drills like the 11-day Exercise Cyber Star with nearly 500 participants from critical information infrastructure sectors such as banking and finance, energy and government.
Operators of critical systems, including those that manage Singapore’s energy, water and transport sectors, must report any suspected APT incidents from later in 2025. This new measure flows from amendments made to the Cybersecurity Act in 2024 to strengthen incident reporting requirements.
Another new cyber threat on the rise that the report highlighted is vishing. This type of cybercrime involves attackers using phone calls or voice messages to deceive people into giving away personal or financial information.
The number of vishing attacks detected globally by cyber-security firm CrowdStrike jumped from two in January 2024 to 93 in December 2024, the report said.
“In most 2024 vishing campaigns, threat actors impersonated IT support staff, calling targeted users under the pretext of resolving connectivity or security issues,” the report added.
Another global cyber-threat trend highlighted is the rise of distributed denial-of-service (DDoS) attacks. These incidents see attackers flooding servers with internet traffic to prevent users from accessing online services.
Cyber-security firm Cloudflare, which contributed insights to the report, said DDoS attacks rose in sophistication and volume, driven in part by powerful botnets spun up by generative artificial intelligence (AI). “Countries in Asia led the DDoS rankings, comprising 60 per cent of the most attacked locations globally,” said Mr Omer Yoachimik, senior product manager for DDoS protection and security reporting at Cloudflare.
The report pointed out that Singapore ranked as the third-largest source of DDoS attack traffic.
CSA pointed out that Singapore’s high concentration of data centres and cloud infrastructure is often exploited as a launch pad for cyber attacks by overseas threat actors.
“By recognising the unique position Singapore holds as a digital hub, it serves as a reminder that with our hub status comes the responsibility of ensuring strong cyber hygiene and proactive measures, to prevent our systems from being misused,” said the agency.
Mr David Koh, commissioner of cyber security and chief executive of CSA, said that while the agency has worked with domestic and international partners to strengthen Singapore’s cyber security, malicious and advanced threat actors continue to pose a danger to the country’s national security, digital economy and way of life.
“We have to redouble our efforts, together with our many partners, stakeholders and Singaporeans. And continue to work towards a future where everyone can live and work online in a trusted, resilient and vibrant cyberspace,” he said.




