WannaCry ransomware: Critical sectors not affected at end of Monday
Sign up now: Get ST's newsletters delivered to your inbox
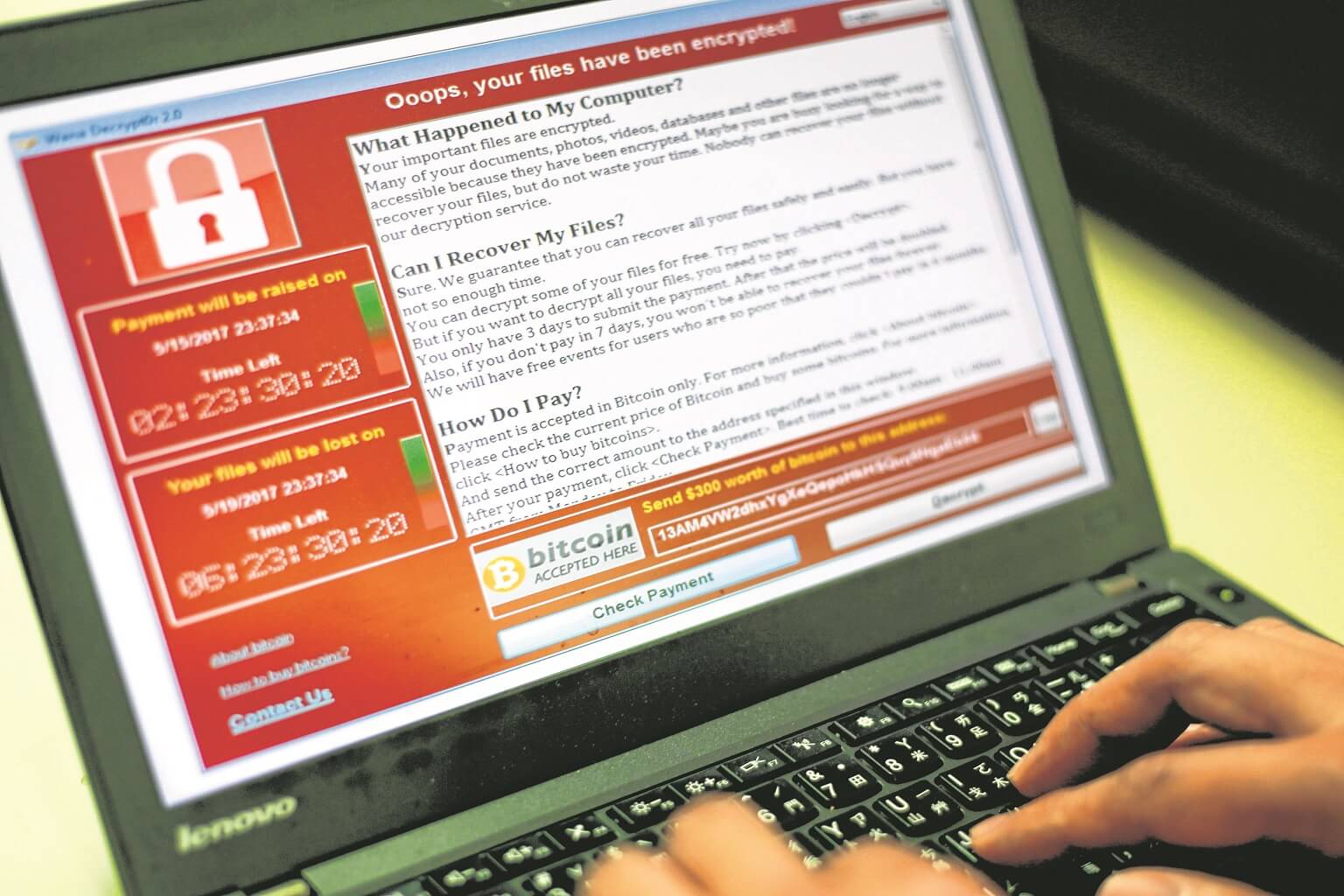
A programmer shows a sample of a ransomware cyberattack on a laptop in Taipei, Taiwan, on May 13, 2017.
PHOTO: EPA
SINGAPORE - Critical services in healthcare, transport, telecommunications, finance and retail in Singapore emerged unscathed on Monday, said the Cyber Security Agency (CSA) of Singapore, even as the global ransomware attack affected over 100 countries worldwide.
Dubbed WannaCry, variants of the worm started attacking Microsoft Windows machines last Friday (May 12). Experts had warned that there could be more fallout on the first day of the work week from the spread of the virus.
Said Mr Dan Yock Hau, director of the National Cyber Incident Response Centre, said in a statement late Monday: "As of this afternoon, no critical information infrastructure has been affected."
The centre is a unit of the CSA, which said it will continue to monitor the situation closely together with the critical sectors here.
"We are also tracking other sources of intelligence and has reached out to offer assistance to those that were brought to our attention," said Mr Dan.
"CSA's National Cyber Security Monitoring Centre also monitors the developing global situation and track the technical indicators to assess the potential implication to Singapore so that we are able to work on the necessary responses and measures to take," he added.
Businesses and members of the public can also refer to SingCert's advisory on WannaCry at www.csa.gov.sg/singcert. They can also seek help from SingCERT through singcert@csa.gov.sg or call 6323 5052.
Over the weekend, infected systems were locked down with a note demanding for ransom, crippling hospitals in England and Scotland and some operations of international shipper FedEx and energy giant PetroChina.
French automaker Renault halted production in several of its factories, while German railway company Deutsche Bahn's information screens and ticket machines could not work.
One victim in Singapore was MediaOnline, which supplies digital signage to malls such as Tiong Bahru Plaza and White Sands.
Ms Karen Siow, general manager of Tiong Bahru Plaza, Liang Court and Hougang Mall at Asia Malls, said: "There is no other anticipated impact from this malware as the digital directory systems run on a separate network from the rest of the corporate networks of AsiaMalls."
Victims either did not apply a software patch, released in March (2017), to fix a known flaw in their Microsoft Windows systems, or were using old, unsupported systems such as Windows XP or Windows Server 2003.
Users might have initially been infected by clicking on a bogus link or attachment in the e-mail. Then the worm spreads to multiple machines over the intranet or Internet using a capability believed to have been developed by the United States National Security Agency - causing the attack to be unprecedented in scale by any ransomware.
Infected systems display a ransom note demanding for US$300 (S$420) to be paid in the bitcoin cryptocurrency within three days, or double the amount in seven days, failing which the encrypted file will be deleted.
A Twitterbot that tracks the ransom payments in real time recorded more than US$42,000 paid to date.
Last year (2016), security software firm Symantec recorded more than 463,000 ransomware attacks, up by a third from 340,000 attacks in 2015. Singapore was ranked the 24th top ransomware destination in 2016, after jumping 18 places from the previous year.
Security experts have urged organisations to keep their security software and operating systems up-to-date to protect themselves against known threats. Organisations have also been advised to regularly back up important data to thwart ransomware criminals.
Additional reporting by Melissa Lin


