Surge in low-level hacking of critical infrastructure
Cyber-security firm warns that even dud attempts are cause for concern
Sign up now: Get ST's newsletters delivered to your inbox
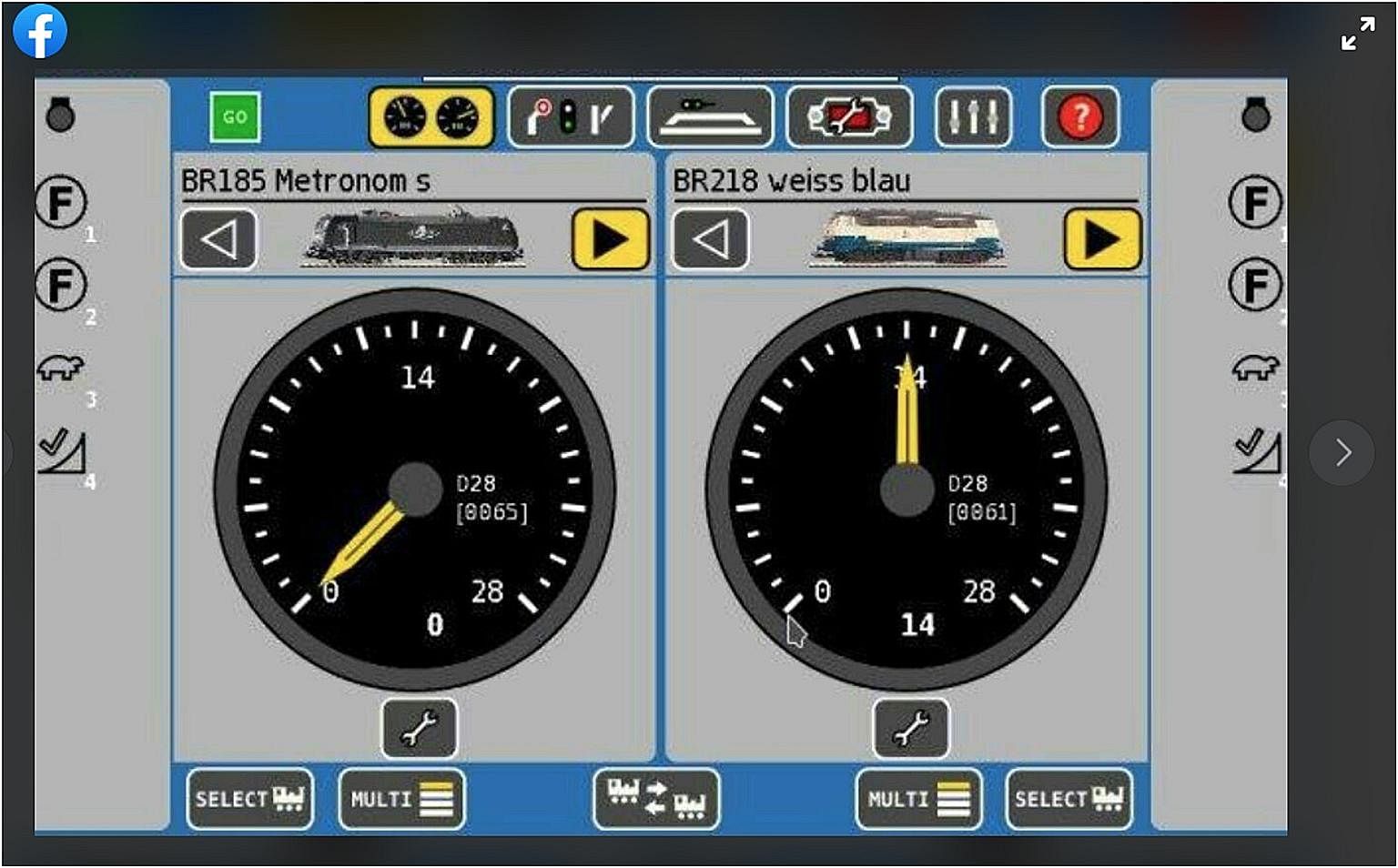
One hacking group claimed it compromised a German-language rail control system, but Mandiant found out that the image of the attacked system was actually a Web interface designed for model train sets.
PHOTO: MANDIANT
Kenny Chee
Follow topic:
Low-level attempts to hack systems that control critical infrastructure, such as in the energy and water sectors, have increased globally by about three to five times in the last few years.
A report by US cyber-security firm Mandiant says the online attacks have become more severe, with even dud attempts now cause for concern.
The systems targeted control infrastructure like solar energy panels, building ventilation and that for water supplies.
Mandiant, part of FireEye, said such hits have risen since 2015. "The severity of incidents has dramatically escalated from almost exclusive attempts to buy and sell access to devices in 2015, to multiple cases of (threat) actors interacting with industrial processes between 2020 and now," Mr Nathan Brubaker, a senior manager at Mandiant Threat Intelligence, told The Straits Times.
Such interactions were not as apparent in the past.
Last month, Colonial Pipeline, which supplies about 45 per cent of fuel used on the East Coast of the United States, was hit by a ransomware attack.
Later that same month, a cyber attack on the world's largest meat processor, Brazilian food giant JBS, forced the closure of all its beef plants in the US - accounting for almost a quarter of supplies in the country - and slowed pork and poultry production.
Mandiant's report, released late last month, said hackers likely did not target specific sectors in their low-sophistication attacks on operational technology systems. This is because they used search engines to scan for any exposed infrastructure online. Unsecured services to access control systems remotely were often exploited.
One possible reason for more such attacks could be the rise in the number of systems online, said Mr Brubaker.
More information has also been made available online for operational technology systems that hackers could use to hone their skills for more attacks.
Utilities, particularly the smaller ones, were often targeted, mostly because of the higher visibility gained from attacking them. "These were typically smaller utilities, so they probably had fewer resources to put towards security programs," Mr Brubaker said.
Some hackers targeted specific regions or countries, such as Israel, but Mandiant did not observe any aimed at Singapore.
Some hackers had political motives and a few would share hacking tutorials with others. But others were in it for the money or to become notorious.
Hackers usually tried to access systems through user-friendly graphical interfaces that allowed them to modify controls without the need for existing knowledge about the processes.
Many hackers also flaunted their handiwork. One group shared images as evidence that it had compromised dozens of control systems in North America, Western and Central Europe, and East Asia, including a video for a hit on a Dutch-language temperature control system.
But some cybercrooks either had limited understanding of operational technology systems or were simply trying to brag.
One hacking group claimed that it compromised a German-language rail control system. But Mandiant later found out that the image of the attacked system was actually a Web interface designed for model train sets.
Even so, Mr Brubaker warned that any unauthorised access to operational technology systems remained worrying, saying: "It may be blind luck that these actors accessed a toy rail system rather than a real one. The more threat actors interact with operational technology and learn about it, the more dangerous their future activities will be."
The attacks that Mandiant detected did not cause physical damage, because of the many fail-safes built into most industrial processes. But, with more attacks, even low-level ones, the risk of physical disruption rises, the firm said.
The publicity around these incidents may also encourage other hackers to target operational technology systems.
Mandiant has advised organisations to put in place best practices for security, such as looking out for unusual activity involving remote access to their infrastructure.

