How scammers posing as SingPost trick victims with SMSes, fake sites
Sign up now: Get ST's newsletters delivered to your inbox
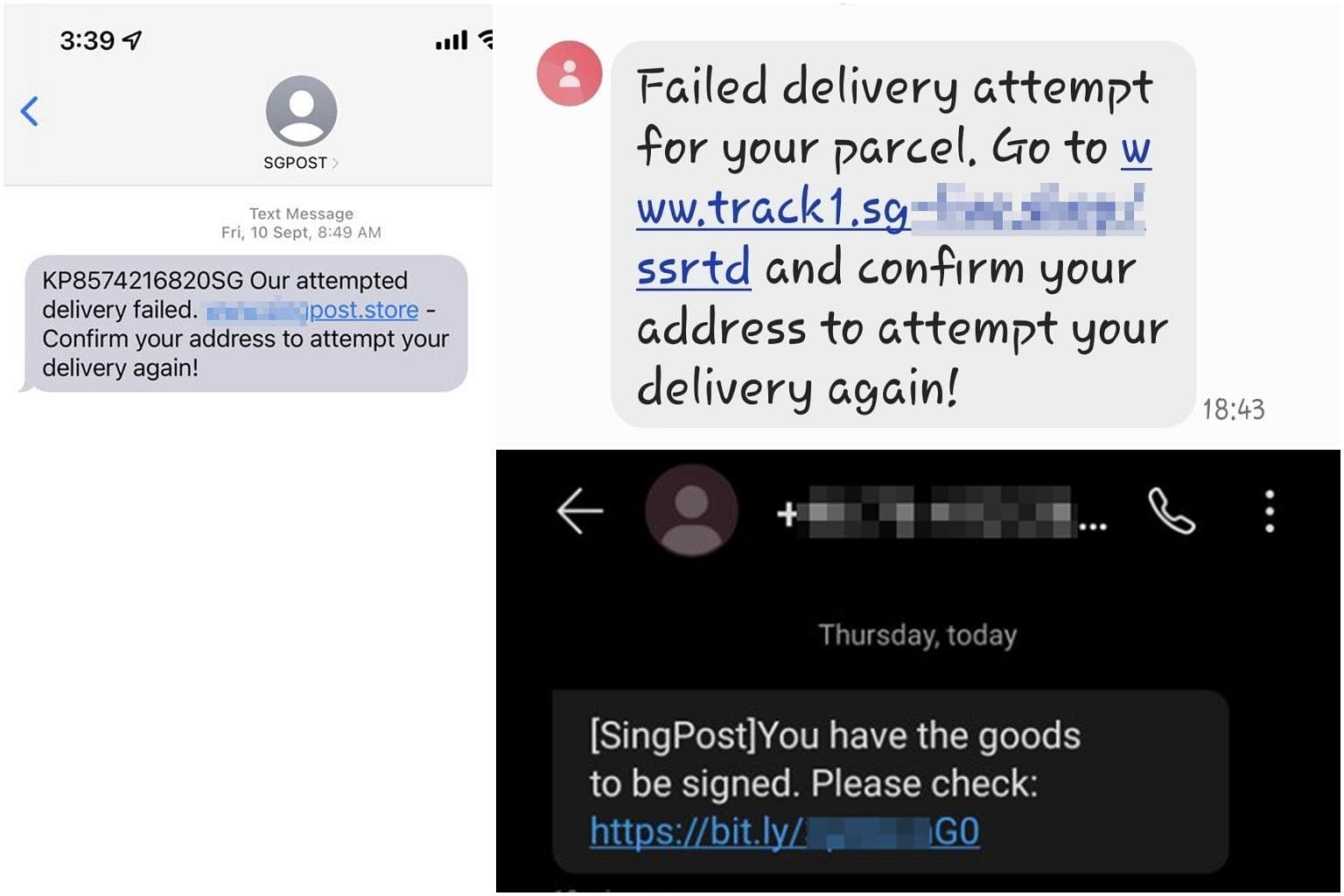
Screenshots of a fake SingPost SMSes used in a scam.
PHOTOS: GROUP-IB
SINGAPORE - The website seems legitimate - it looks like the site of postal services company Singapore Post. It even displays a scam alert that reads: "Phishing websites impersonating SingPost are using fake delivery notices and text messages to extract personal data."
In reality, this site is itself a scam site phishing for victims' details. This was among three types of phishing scams by fraudsters masquerading as SingPost uncovered by cyber-security firm Group-IB.
According to data released by the police last month, victims lost a whopping $15.3 million last year from phishing scams not related to banks, an over 15-fold spike from 2020's $984,000.
Of these non-bank related phishing scams, one prominent type involved crooks posing as delivery companies such as SingPost.
Group-IB said on Monday (March 28) that the three scam types use fake SMSes and sites that appear to belong to SingPost. It is unclear where the scammers are from. Here are more details about these scams.
Q. How do the fake SMSes try to pass off as SingPost texts?
A: The SMS sender names used by the fraudsters for the fake texts included "info", "msginfo", "SMSinfo" and "AUTHMSG". But some used more genuine-looking names such as "SingPost" and "SGPOST".
The bogus texts look like delivery notices encouraging victims to click a shortened URL leading to a fake SingPost site. For instance, the SMSes cite a delivery problem that needs to be resolved at the URL provided, or name-drop SingPost and say goods need to be signed.
Q. How do the fake SingPost sites trick victims?
A: The three scams have some differences in their tactics. In the first SMS scam type - dubbed Group 1 - after the victim is tricked into clicking the link in a fake delivery notice SMS, they are directed to a fake SingPost site that asks them to leave a phone number and pay a small fee to receive a delivery.
The fake site tries to look more legitimate by having a scam alert warning the victim about phishing sites impersonating SingPost.
"The scam alerts on the rogue websites are something that we've been seeing for a while all over the world," said Mr Ilia Rozhnov, Group-IB's head of the digital risk protection team in the Asia-Pacific. "In Singapore, we detected this tactic for the first time in 2021. A scam alert itself cannot be used to verify the legitimacy of the website."
The scam eventually directs victims to a fake payment site where they are tricked into entering payment and personal details. They also get subscribed to monthly payments of $40 to $60 to the fraudsters, but these transactions tend to go unnoticed by traditional anti-fraud solutions.
The first known Group 1 scam sites appeared between March and April 2020. At the scam's peak, there were at least 15 fake SingPost sites but none is active now.
Mr Rozhnov said the fake sites do not remain active for long, with the fraudsters moving quickly between different fake sites. Inactive sites can get reactivated later, too.
In the second scam type, called Group 2, the crooks' fake SMS leads victims to a site saying an upgraded version of the Chrome Web browser is needed and directs them to download malware disguised as Chrome.
If installed, the malware can intercept SMSes like those for one-time passwords (OTPs), steal a victim's phone contact list, and send SMS spam to those on the list.
Group 2 scams were active from September 2020 to June last year, with over 80 fake sites, none of which is active now.
In the third scam type, Group 3, SMSes are believed to be used to lure the victim to visit a fake site, where he gets asked to pay a small fee to receive a parcel.
Scammers use payment details the victim entered into the fake site on a real banking site to carry out a fraudulent transaction. This triggers an SMS OTP to be sent to the victim to verify the scam transaction. The fake site also asks the victim for the OTP. If entered, the password is used by the crooks to verify their transaction and drain the victim's bank account of funds.
Group 3 scams have been active since September last year, with more than 90 fake SingPost sites. Just one site is currently active.
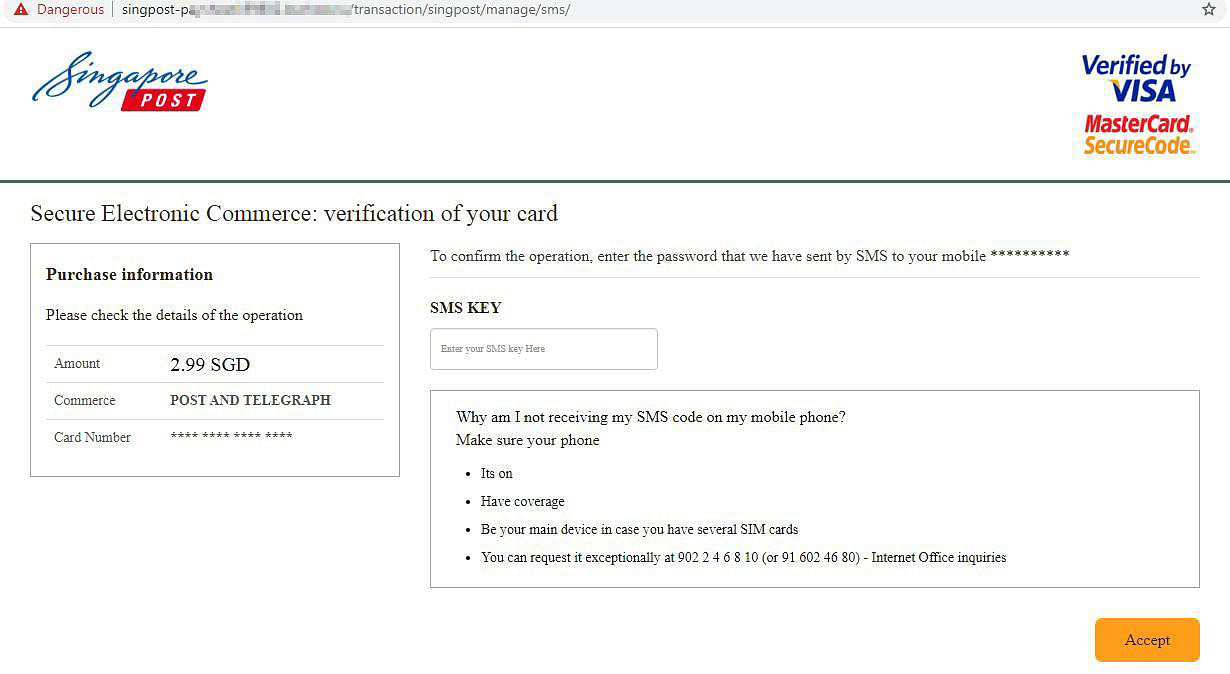
knscam29 - A fake SingPost website used in a scam to try and trick victims into sharing their one-time passwords with the fraudsters. Source/credit: Group-IB
PHOTO: Group-IB
Q. How can I protect myself from such scams?
A: Group-IB advises consumers to be careful about clicking links in SMSes and e-mails, regardless of who the messages are from, since scammers can spoof a legitimate sender's number and e-mail address. The crooks might even use victims' names and other personal data to appear more legitimate.
Consumers should only use official websites to track their parcels and to verify information.
They should not allow third-party sources to install programs on their devices and should download apps only from trusted sources.
SingPost would also not send SMSes with links because the postal services company has stopped doing so since Feb 28.
If you have information on phishing scams, you can call the police hotline on 1800-255-0000 or submit it online at this website. If you require urgent police assistance, call 999.
To get advice on online scams, visit the Scam Alert website or call the police's anti-scam hotline on 1800-722-6688.


