Task force publishes report on how govt, institutions and firms in S’pore can defend against ransomware
Sign up now: Get ST's newsletters delivered to your inbox

Attackers typically make first contact through social engineering ploys, luring users to download malicious software.
ST PHOTO ILLUSTRATION: KEVIN LIM
SINGAPORE – An inter-agency crack team commissioned to help businesses and national institutions tackle ransomware threats has published its first report, which breaks down how such attacks unfold and ways to fight them.
The task force also made recommendations to the Government on how it could counter successful ransomware attacks, such as by making it mandatory for victim organisations to report the payment of ransom.
It also urged the authorities to adopt a global approach by engaging international law enforcement partners and called on companies to identify critical assets while also segregating their networks, keeping these assets separate.
The Counter Ransomware Task Force (CRTF), which released its inaugural report on Wednesday, comprises senior officers from the Cyber Security Agency (CSA) of Singapore, Government Technology Agency, Infocomm Media Development Authority, Ministry of Communications and Information, Ministry of Defence, Ministry of Home Affairs, Monetary Authority of Singapore, Singapore Armed Forces and Singapore Police Force. It is also supported by the Attorney-General’s Chambers.
The team was set up earlier this year.
Minister for Communications and Information Josephine Teo said the report is a blueprint for Singapore to counter ransomware attacks, which are on the rise globally. The number of ransomware cases reported grew from 89 in 2020 to 137 in 2021, according to CSA.
The task force said: “The problem of ransomware is urgent, even existential, for all digitally connected countries, including Singapore. Recent attacks have shown that ransomware attacks have the potential to become serious threats to a nation’s national security, economic security and critical information infrastructure.”
It added: “Attackers have raised their ambitions, and are starting to target large companies, essential supplies and services, even governments, in hope of eliciting a larger ransom.”
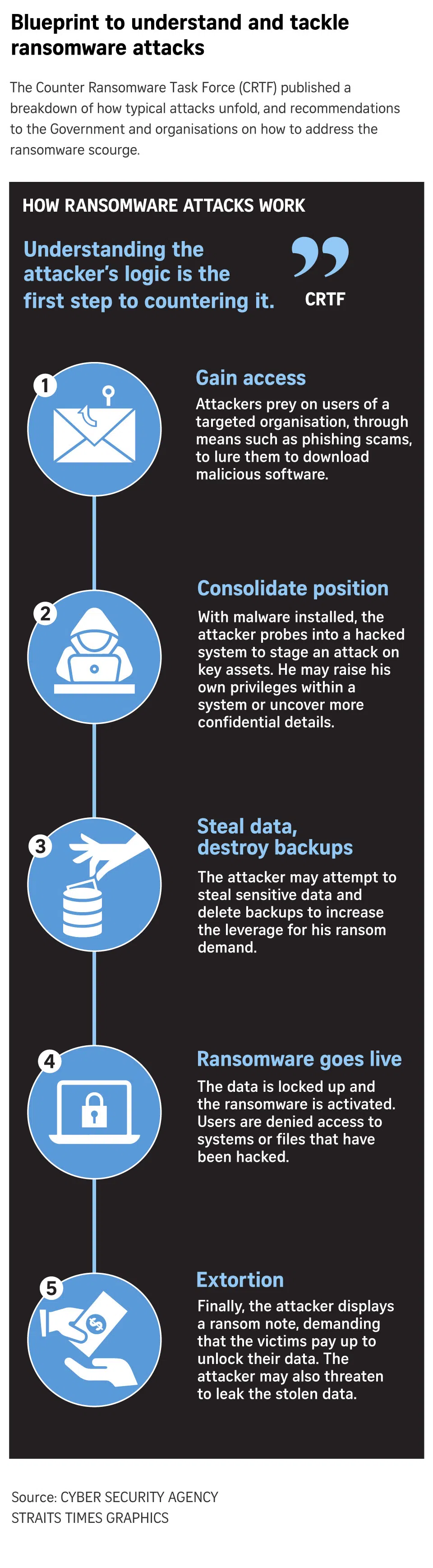
The CRTF detailed a typical attack in a sequence dubbed the “ransomware kill chain”.
Attackers typically make first contact through social engineering ploys, like a phishing scam, luring users from a target organisation to download malicious software.
Once in, they comb through a system for credentials like passwords, and escalate their privileges to take control of a network as part of the second phase of the attack.
The attackers may then steal or lock up sensitive information that a victim organisation cannot bear to lose, and delete backups, increasing leverage for their ransom demand.
With the stage set, the attacker leaves a ransom note to demand payment. Hackers may also threaten to leak stolen data, such as medical records or banking credentials, to hasten victims to pay.
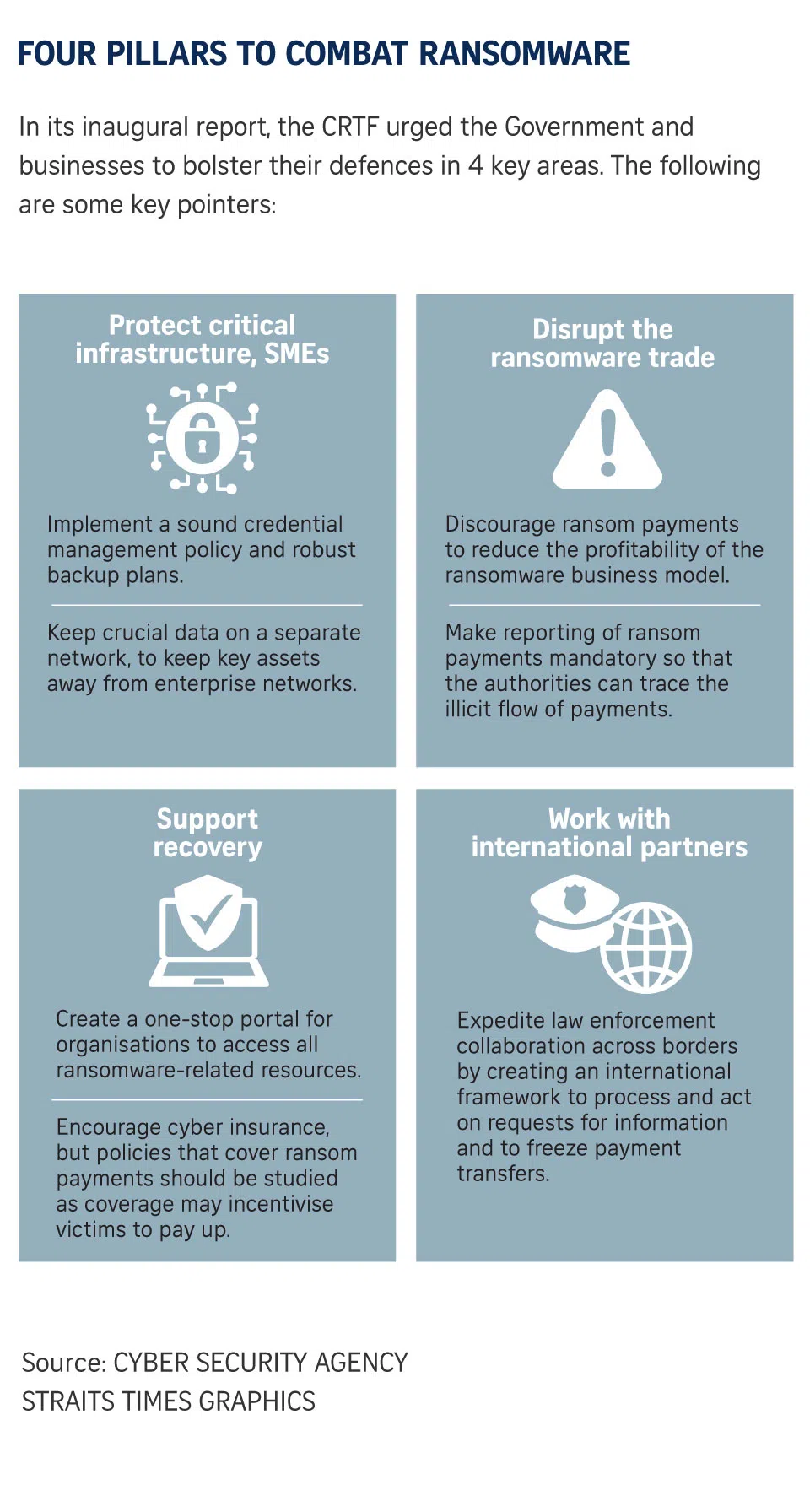
Organisations should reduce the chances of attackers advancing past the second phase, before the data is stolen or encrypted, by ramping up cyber-security measures, said the CRTF.
They can do this through the use of takedown measures such as the protective domain name service (pDNS). Endorsed by the United States National Security Agency, the pDNS software actively monitors activity on a server and takes action to mitigate threats.
The CRTF’s report identifies actionable strategies for the authorities engaged in combating ransomware. It said that the authorities should reduce the profitability of ransomware attacks for hackers by discouraging ransom payments.
Paying ransom does not guarantee that hackers will not publish the stolen data, and might motivate them to attack the company again, now that it is seen as a “soft” target, the report added.
The CRTF took aim at cyber-security insurance policies that specifically include coverage for the payment of ransoms, as victims may be incentivised to cave in to hackers’ demands, knowing that they will be compensated.
Such payments play a part in fuelling the ransomware industry, and studies need to be made on the potential effects of disallowing such insurance coverage, said the CRTF.
It added that cyber insurance was still crucial, especially for critical infrastructure operators and enterprises, urging the Government to explore ways to increase the take-up rate in such organisations.
Organisations should be required to report the payment of ransoms to the Government, said the CRTF, so that the authorities can trace the illicit flow of payments, often made in cryptocurrency.
The CRTF also urged companies to identify critical assets in their inventories and subject them to more stringent security measures. It urged firms to have a sound credential management policy, such as multi-factor authentication on key assets, and a backup and restoration plan.
The report recommended that company networks be segregated on the basis of the security level required, preventing key assets from being mixed with other networks.
Lastly, the authorities were urged to adopt a global approach to countering ransomware by engaging international partners, to expedite cross-border law enforcement efforts to stem ransom payments.
Ransomware attacks can result in disastrous consequences should critical services be paralysed by a hack.
In May 2021, a ransomware attack on the Colonial Pipeline Company