S’pore’s four major telcos came under attack by cyberespionage group UNC3886 in 2025
Sign up now: Get ST's newsletters delivered to your inbox

Singtel, StarHub, M1 and Simba Telecom came under attack but no sensitive data was accessed or exfiltrated. Critical systems were also not compromised.
PHOTOS: ST FILE, GIN TAY
- Singapore's four major telcos (Singtel, StarHub, M1, Simba) were targeted by cyber espionage group UNC3886.
- UNC3886 exploited a zero-day vulnerability and used malware like Medusa to steal credentials and access internal telco systems, exfiltrating technical data.
- Operation Cyber Guardian was launched, and Singapore implemented measures such as enhancing detection, redesigning networks, and purple teaming to protect infrastructure.
AI generated
SINGAPORE - All four major telcos in Singapore came under attack by state-sponsored cyberespionage group UNC3886, whose activities to disrupt critical services here were first made public in July 2025
No sensitive data was accessed or exfiltrated, and critical systems such as the 5G core were also not compromised, said the authorities.
Revealing for the first time on Feb 9 that Singtel, StarHub, M1 and Simba Telecom were the targets, Minister for Digital Development and Information Josephine Teo said: “Our investigations show that the attacks by UNC3886 were a deliberate, targeted and well-planned campaign against our telecommunications companies.”
Mrs Teo was speaking at an event honouring the efforts of cyberdefenders against UNC3886 at the Cyber Security Agency of Singapore’s (CSA) office in Punggol Digital District.
Investigations showed that the attackers were able to extract a small amount of technical data. While they had accessed a few critical systems, they did not get far enough to disrupt services, she said.
The Infocomm Media Development Authority (IMDA) and CSA said the most sensitive and critical systems such as 5G networks were locked away separately, and were not compromised.
While no sensitive data was stolen, Mrs Teo said the attacks cannot be taken lightly.
“First, they were more capable of accessing sensitive information for espionage. Second, they could deploy more tools to disrupt telecoms and internet services. Everything that requires a phone or internet connection would then be affected,” she said.
“The knock-on effects of their campaign could also have included other essential services like banking and finance, transport and medical services,” added Mrs Teo, who is also Minister-in-charge of Cybersecurity and Smart Nation Group.
UNC3886 was first detected in 2022
The Chinese Embassy here denied involvement in the Singapore attack and said China cracks down on all forms of cyberattacks in accordance with the law.
Damage caused by compromised telco infrastructure could be devastating.
Mrs Teo cited an example in South Korea where the SIM data of nearly 27 million users was exposed after telco SK Telecom was attacked in April 2025.
Also in 2025, the authorities in the United States reported that advanced persistent threat (APT) group Salt Typhoon had infiltrated a large number of US telecommunications providers and may have obtained sensitive military or law enforcement information.
Mrs Teo said that successful cyberattacks can affect trust and confidence in Singapore as an international financial and logistics centre. Multinational companies also choose to house their global headquarters here because of Singapore’s safe and reliable digital connectivity.
“Businesses may shy away from Singapore if they are unsure about our systems – whether the systems are clean, resilient and safe,” she said.

Minister for Digital Development and Information Josephine Teo (third from left) and CSA chief executive David Koh (left) viewing the technical demonstration during engagement event for cyberdefenders on Feb 9.
ST PHOTO: CHONG JUN LIANG
Urging everyone to be vigilant, Mrs Teo underscored the importance of the work of cyberdefenders and early communication.
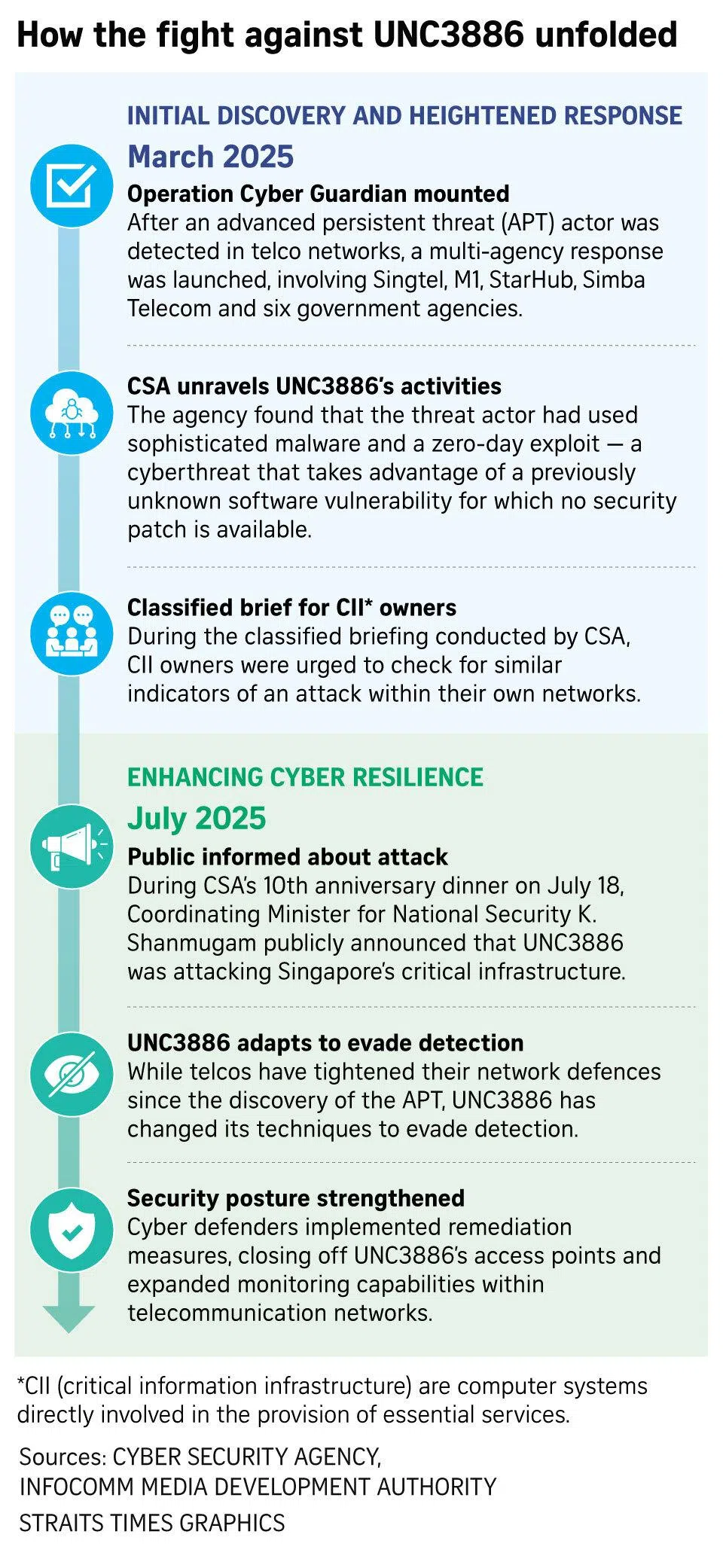
Even though suspicious activities detected by the telcos in March 2025 did not reach the threshold required for sounding the alarm, they reported the anomalies to CSA.
This allowed a multi-agency effort, code-named Operation Cyber Guardian, to be mounted for the first time.
It is Singapore’s largest coordinated cyberresponse to date, involving more than 100 cyberdefenders across six government agencies. The agencies are: CSA, IMDA, the Singapore Armed Forces’ Digital and Intelligence Service, Centre for Strategic Infocomm Technologies, Internal Security Department and Government Technology Agency of Singapore.
“So far, our attackers have not been able to move deeper into our telco networks,” said Mrs Teo.
Investigations found that UNC3886 gained initial access through a zero-day vulnerability – a hidden flaw with no known fix – at the perimeter firewall, akin to “finding a new key no one else had found to unlock the doors”, she said.
Other defensive actions taken to protect the telco infrastructure include enhancing detection measures, and redesigning the network and hardening telcos’ systems to impede further attacks.
Purple teaming – where simulated attacks and defences take place to improve an organisation’s security – was done to validate that the remediation measures were working.
But Mrs Teo warned that despite best efforts, there is no guarantee against future, continuing attempts to gain access to Singapore’s critical infrastructure.
APTs are backed by countries with formidable resources in manpower and technology, and will not give up so easily.
“In short, the fight continues, and we must all do our part,” said Mrs Teo.
She also called on critical infrastructure operators, many of which are private companies, to continue investing in upgrading their systems and capabilities.
“You are at the front lines of the battle against cyberthreat actors. Your actions, or inaction, can determine whether we succeed or fail in protecting our critical infrastructure, and our national security,” said Mrs Teo.
In a joint statement, the four telcos said that all operators face cyberthreats such as distributed denial of service attacks, malware, phishing, and now, increasingly sophisticated, advanced and persistent threats.
“We adopt defence-in-depth mechanisms to protect our networks and conduct prompt remediation when vulnerabilities are detected. We also work closely with government agencies and industry experts to improve our security and resilience,” said the telcos.
They added that protecting critical infrastructure is their top priority, and they will keep pace with the cyberthreat landscape.



