How S’pore defended its telcos against cyberespionage group UNC3886: A timeline
Sign up now: Get ST's newsletters delivered to your inbox

Operation Cyber Guardian set off Singapore’s largest cybersecurity operation that involved more than 100 defenders from the telcos and six government agencies.
PHOTO: LIANHE ZAOBAO
SINGAPORE – Four local telcos were targeted in the 2025 attack Singapore’s largest cybersecurity operation that involved more than 100 defenders
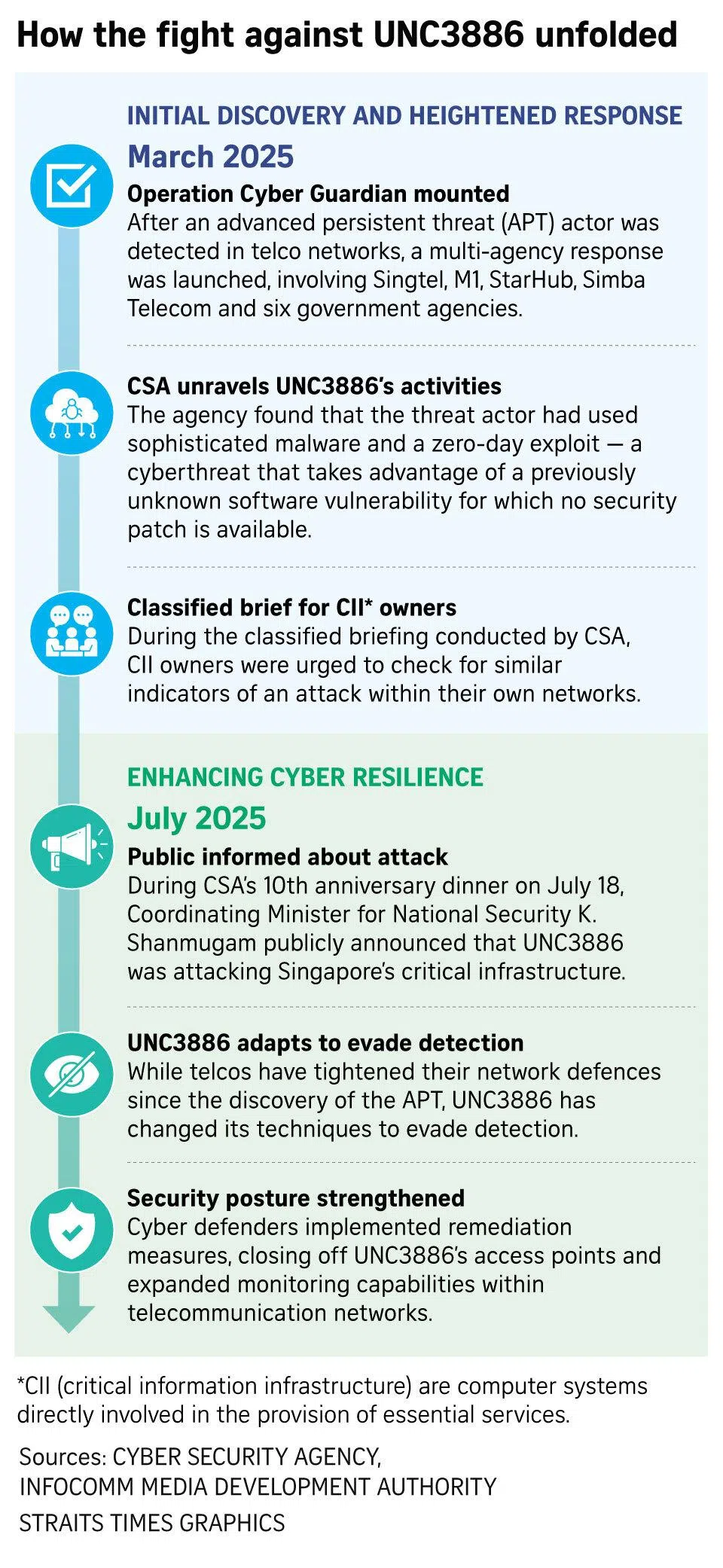
Here’s how Operation Cyber Guardian unfolded.
March 2025
The presence of an advanced persistent threat actor was detected in local telecommunication networks operated by Singtel, M1, StarHub and Simba Telecom.
This led to the launch of Operation Cyber Guardian – which involved more than 100 cyberdefenders from the telcos and six government agencies – the Cyber Security Agency of Singapore (CSA), the Infocomm Media Development Authority, the Centre for Strategic Infocomm Technologies, the Singapore Armed Force’s Digital and Intelligence Service, the Government Technology Agency of Singapore (GovTech) and the Internal Security Department.
In spearheading the multi-agency operation, CSA began investigating UNC3886’s activities, including the use of sophisticated malware and a zero-day exploit. This refers to a cyberthreat that takes advantage of a previously unknown security vulnerability in software, for which there is no available security patch.
CSA also held a classified briefing for owners of Singapore’s critical systems, reminding them to check for similar indicators of an attack within their own networks.
July 2025
During CSA’s 10th anniversary dinner on July 18, Coordinating Minister for National Security K. Shanmugam named the attacker publicly for the first time
“UNC3886 poses a serious threat to us, and has the potential to undermine our national security,” said Mr Shanmugam. He stopped short of disclosing UNC3886’s sponsors, but experts have said that the group is linked to China.
When telcos began to tighten their network defences after detecting UNC3886, the threat actor began to change its techniques to evade detection. This includes the use of rootkits, which is stealthy, malicious software that hides its presence. It provides threat actors with persistent, hidden admin-level access and disables security features such as anti-virus software.
UNC3886 was able to gain unauthorised access to servers that manage and maintain internal telco systems. However, IMDA said in a statement on Feb 9 that there is no evidence that sensitive or personal data such as customer records were accessed or exfiltrated.
There is also no evidence that the threat actor managed to disrupt telecommunications services such as internet availability, said IMDA.
Cyberdefenders implemented remediation measures, closing off UNC3886’s access points, and expanded monitoring capabilities within telecommunication networks.