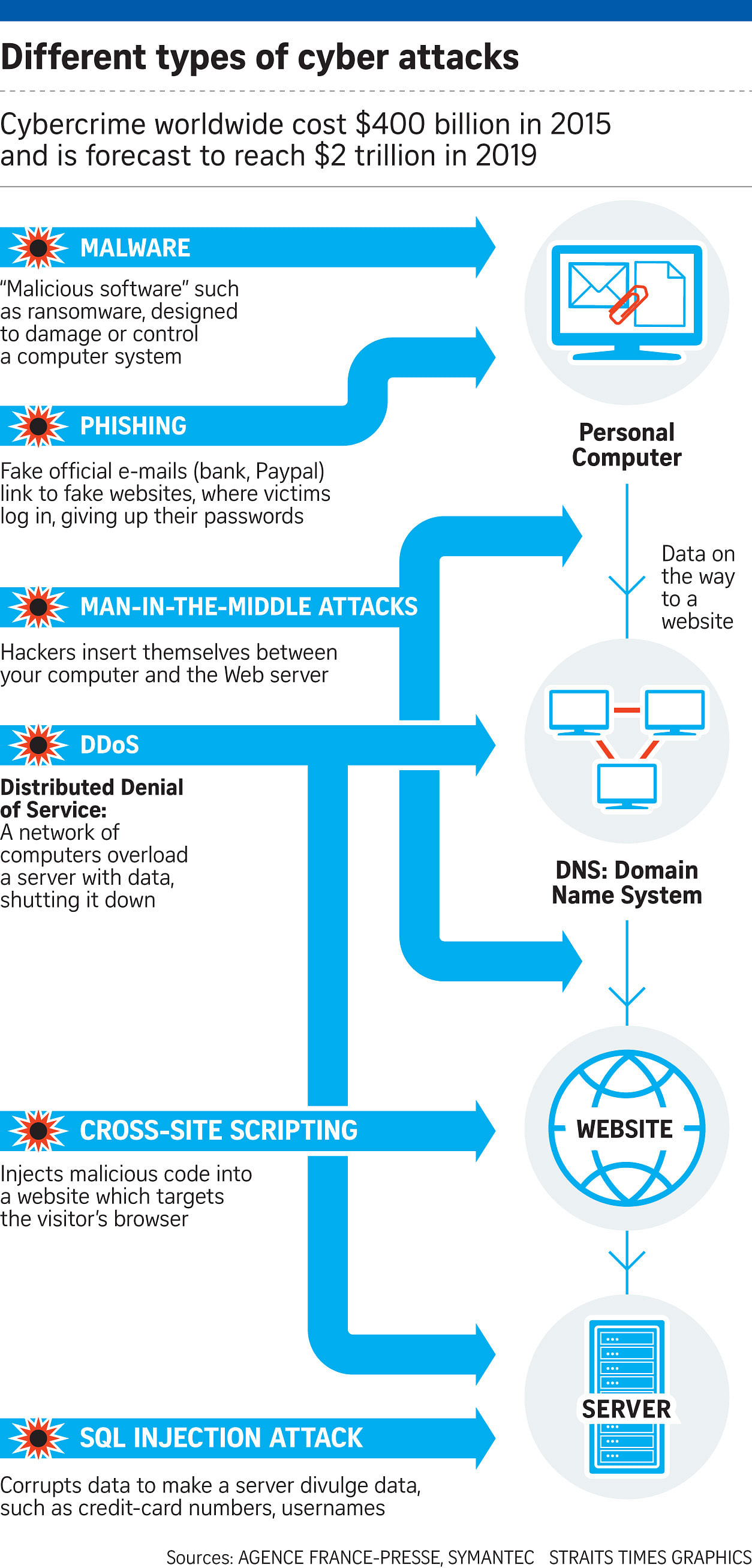
KIEV • A cyber attack wreaked havoc around the globe, crippling thousands of computers, including disrupting port operations in Mumbai and halting production at a chocolate factory in Australia.
The virus is believed to have first taken hold on Tuesday in Ukraine, where it silently infected computers after users downloaded a popular tax accounting package or visited a local news site, national police and international cyber experts said.
The malicious code locked machines and demanded that victims post a ransom worth US$300 (S$410) in bitcoins or lose their data entirely.
More than 30 victims paid up, but security experts are questioning whether extortion was the goal, given the relatively small sum demanded, or whether the hackers were driven by destructive motives rather than financial gain.
Some IT specialists identified the virus as NotPetya, a modified version of the Petya ransomware which circulated last year.
Ukraine, the epicentre of the latest attack, has repeatedly accused Russia of orchestrating attacks on its computer systems and critical power infrastructure since its powerful neighbour annexed the Black Sea peninsula of Crimea in 2014.
The Kremlin, which has consistently rejected the accusations, said yesterday that it had no information about the origin of the global cyber attack, which also hit Russian companies such as oil giant Rosneft.
ESET, a Slovakian company that sells products to shield computers from viruses, said that 80 per cent of the infections detected among its global customer base were in Ukraine, and Italy was the secondhardest hit with about 10 per cent.
The aim of the latest attack appeared to be disruption rather than ransom, said Mr Brian Lord, former deputy director of intelligence and cyber operations at Britain's GCHQ intelligence agency, and now managing director of private security firm PGI Cyber.
''My sense is this starts to look like a state operating through a proxy... as a kind of experiment to see what happens,'' Mr Lord said.
Cyber researchers have tied the vulnerability exploited by the virus to the one used by WannaCry - a weakness discovered by the US National Security Agency years ago that the agency turned into a hacking tool dubbed EternalBlue.
But experts noted that it was not as virulent as last month's Wanna- Cry attack. They said Tuesday's virus could leap from computer to computer once unleashed within an organisation but, unlike WannaCry, it could not randomly trawl the Internet for its next victims, limiting its scope to infect.
The introduction of security patches in the wake of the May attack that crippled hundreds of thousands of computers also helped to curb the latest malware, though its rapid spread underlined concerns that some businesses have still not secured their networks from increasingly aggressive hackers.
After WannaCry, unleashed by hackers possibly linked to North Korea, governments, security firms and industrial groups advised businesses and consumers to make sure all their computers were updated with Microsoft security patches.
Austria's government-backed Computer Emergency Response Team said ''a small number'' of international firms appeared to be affected, with tens of thousands of computers taken down.
The onslaught of ransomware attacks may be the ''new normal'', according to Mr Mark Graff, chief executive of Tellagraff, a cybersecurity company.
-
NotPetya and WannaCry: How they stack up
-
BOTH USE THE 'PHISHING' METHOD
NotPetya and WannaCry infect computers using a method known as "phishing" to get unsuspecting e-mail users to click on booby-trapped attached Office documents.
The documents, once opened, will download and run the WannaCry or NotPetya installer and push the worm to spread to other connected computers. Infected systems are locked down with a note demanding a ransom.
BOTH INFECT THROUGH ETERNAL BLUE
United States-based security software firm Symantec confirmed that NotPetya was infecting computers through at least one system vulnerability known as Eternal Blue.
Eternal Blue, a hacking tool used by the National Security Agency, was leaked online in April by a group of hackers known as the Shadow Brokers.
The same vulnerability was used last month to spread WannaCry, which infected hundreds of thousands of computers in more than 150 countries.
NO KILL SWITCH FOR NOTPETYA
An accidental move by a 22-year-old researcher in Britain, identified as "MalwareTech", activated the kill switch for WannaCry and halted its spread within days.
But there is no kill switch for NotPetya.
NOTPETYA UNLEASHES GREATER DAMAGE THAN WANNACRY
The Singapore Computer Emergency Response Team described NotPetya as "more dangerous and intrusive" than WannaCry.
Unlike WannaCry, which encrypts a computer's files, NotPetya encrypts a segment of the hard drive that renders the entire computer inoperable.
NotPetya also reboots the infected machine to display the ransom message.
''The emergence of Petya and WannaCry really points out the need for a response plan and a policy on what companies are going to do about ransomware,'' he said.
''You won't want to make that decision at a time of panic, in a cloud of emotion.''
The cyber attack mainly targeted Eastern Europe, but also hit companies in Spain, Denmark and Britain. Victims included British advertising and marketing multinational company WPP.
India's biggest container port was also crippled when a Maersk-run terminal in Mumbai was hit. The virus even downed systems at the site of the former Chernobyl nuclear power plant, forcing scientists to monitor radiation levels manually.
In Ukraine on Tuesday, grocery store checkout machines broke down, ATMs demanded ransom payments and the turnstile system in the Kiev metro reportedly stopped working.
The mayhem spread even in the government. Ukrainian Deputy Prime Minister Pavlo Rozenko on Tuesday tweeted a picture of a computer screen warning in English that ''one of your disks contains errors'', then adding in capital letters: ''Do not turn off your PC! If you abort this process, you could destroy all your data!''
REUTERS, WASHINGTON POST
VIDEO
Virus hits European computer servers. str.sg/4EK8