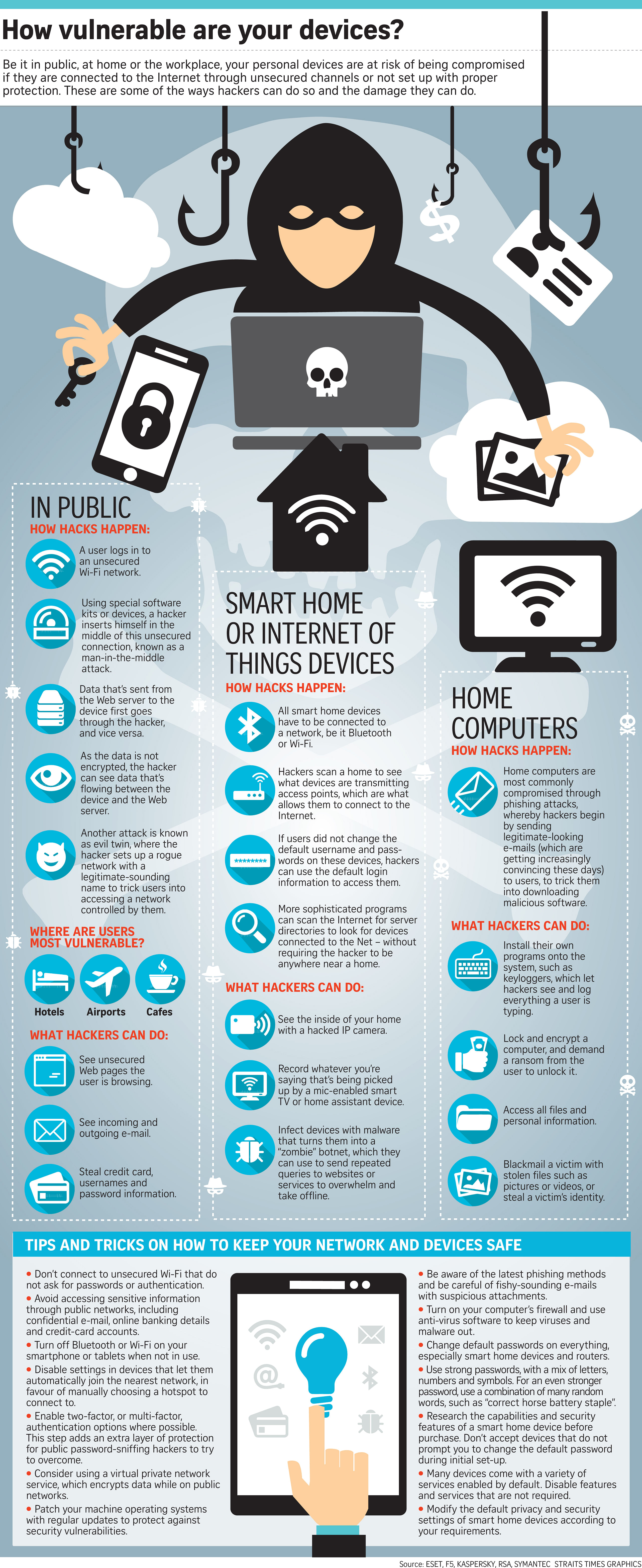
Be it in public, at home or the workplace, your personal devices are at risk of being compromised if they are connected to the Internet through unsecured channels or not set up with proper protection. These are some of the ways hackers can do so and the damage they can do.
In public
How hacks happen:
1. A user logs in to an unsecured Wi-Fi network.
2. Using special software kits or devices, a hacker inserts himself in the middle of this unsecured connection, known as a man-in-the-middle attack.
3. Data that's sent from the Web server to the device first goes through the hacker, and vice versa.
4. As the data is not encrypted, the hacker can see data that's flowing between the device and the Web server.
5. Another attack is known as evil twin, where the hacker sets up a rogue network with a legitimate-sounding name to trick users into accessing a network controlled by them.
Where are users most vulnerable?
Hotels, airports and cafes.
What hackers can do:
1. See unsecured webpages the user is browsing.
2. See incoming and outgoing e-mail.
3. Steal credit card, usernames and password information.
Smart home or internet of things devices
How hacks happen:
1. All smart home devices have to be connected to a network, be it Bluetooth or Wi-Fi.
2. Hackers can scan a home to see what devices are transmitting access points, which are what allows them to connect to the Internet.
3. If users did not change the default username and passwords on these devices, hackers can use the default login information to access them.
4. More sophisticated programs can scan the Internet for server directories to look for devices connected to the Net - without requiring the hacker to be anywhere near a home.
What hackers can do:
1. See the inside of your home with a hacked IP camera.
2. Record whatever you're saying that's being picked up by a mic-enabled smart TV or home assistant device.
3. Infect devices with malware that turns them into a "zombie" botnet, which they can use to send repeated queries to websites of services to overwhelm and take offline.
Home computers
How hacks happen:
1. Home computers are most commonly compromised through phishing attacks, whereby hackers begin by sending legitimate-looking e-mails (which are getting increasingly convincing these days to users, to trick them into downloading malicious software.
What hackers can do:
1. Install their own programs onto the system, such as keyloggers, which let hackers see and log everything a user is typing.
2. Lock and encrypt a computer, and demand a ransom from the user to unlock it.
3. Access all files and personal information.
4. Blackmail a victim with stolen files such as pictures or videos, or steal a victim's identity.
TIPS AND TRICKS ON HOW TO KEEP YOUR NETWORK AND DEVICES SAFE
1. Don't connect to unsecured Wi-Fi that do not ask for passwords or authentication.
2. Avoid accessing sensitive information through public networks, including confidential e-mail, online banking details and credit-card accounts.
3. Turn off Bluetooth or Wi-Fi on your smartphone or tablets when not in use.
4. Disable settings in devices that let them automatically join the nearest network, in favour of manually choosing a hot spot to connect to.
5. Enable two-factor, or multi-factor, authentication options where possible. This step adds an extra layer of protection for public password-sniffing hackers to try to overcome.
6. Consider using a virtual private network service, which encrypts data while on public networks.
7. Patch your machine operating systems with regular updates to protect against security vulnerabilities.
8. Be aware of the latest phishing methods and be careful of fishy-sounding e-mails with suspicious attachments.
9. Turn on your computer's firewall and use anti-virus software to keep viruses and malware out.
10. Change default passwords on everything, especially smart home devices and routers.
11. Use strong passwords, with a mix of letters, numbers and symbols. For an even stronger password, use a combination of many random words, such as "correct horse battery staple".
12. Research the capabilities and security features of a smart home device before purchase. Don't accept devices that do not prompt you to change the default password during initial set-up.
13. Many devices come with a variety of services enabled by default. Disable features and services that are not required.
14. Modify the default privacy and security settings of smart home devices according to your requirements.