NEW YORK (NYTIMES, REUTERS) - Unknown hackers launched simultaneous attacks against computer systems around the world, holding vital information for ransom and throwing government agencies, businesses and hospitals into chaos.
More than 45,000 attacks have been recorded in as many as 74 countries, including Russia, Turkey, Vietnam, the Philippines and Japan, according to Kaspersky Labs, a Russian cybersecurity firm.
Meanwhile, researchers with security software maker Avast said they had observed 57,000 infections in 99 countries with Russia, Ukraine and Taiwan the top targets.
Among the companies and government agencies affected were FedEx, Britain's National Health Service and the Russian Interior Ministry.
WHAT WE KNOW
- Hackers appeared to have exploited a flaw in Microsoft's Windows operating system that was first discovered by the US National Security Agency. The flaw and a tool to exploit it with malicious software were made public in April by a hacker collective known as Shadow Brokers.
- At least 16 British hospitals and other facilities seemed to be hit hardest by the attacks, which blocked doctors from gaining access to patient files and caused emergency rooms to divert patients. Prime Minister Theresa May said there was no evidence that patient data had been compromised.
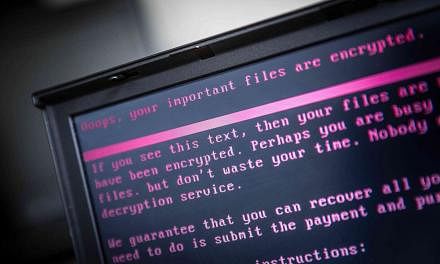
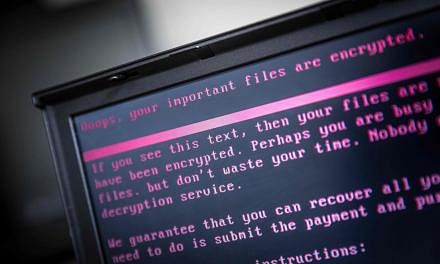
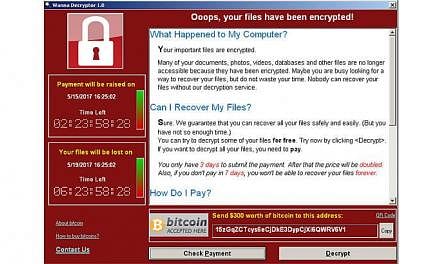
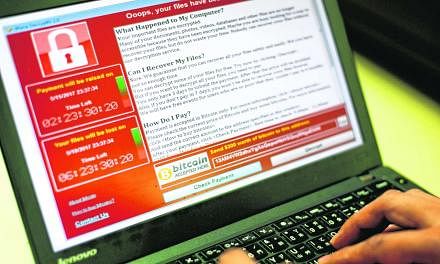
- Workers at those hospitals, a Spanish telecommunications firm and elsewhere were confronted with a message on their monitors that read, "Ooops, your files have been encrypted!" and demanded US$300 (S$421) in bitcoin, an anonymous digital currency preferred by criminals, to restore access.
- The Russian Interior Ministry confirmed in a statement that 1,000 of its computers had also been hit.
- A FedEx spokesman said of the attack: "Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware. We are implementing remediation steps as quickly as possible. We regret any inconvenience to our customers."
- Cybersecurity experts identified the malicious software as a variant of ransomware known as WannaCry.
- Reports last year found that some state-run hospitals in Britain had spent nothing on cyberdefence and were running outdated software on their systems.
WHAT IS RANSOMWARE?
- In a typical attack, hackers send their victims an email that includes a link to what appears to be for an innocuous web address or email attachment. In this case, attackers appear to have sent their victims encrypted .zip file attachments intended to make it more difficult to detect their nefarious purpose.
- Victims who click on that attachment soon find their computers infected. The program encrypts files, folders, and drives on the computer - and potentially the entire networks to which they are connected. "Users and organisations are generally not aware they have been infected until they can no longer access their data or until they begin to see computer messages advising them of the attack and demands for a ransom payment in exchange for a decryption key," according to the FBI.
- The messages that victims receive include directions for paying the attackers a ransom. Payment is typically demanded, as it was in the most recent string of attacks, in bitcoin.
- Microsoft in March recognised a potential flaw in its servers that allowed ransomware and other malicious software to spread on networks.
- A hospital in Los Angeles was similarly attacked in February 2016, paying a bitcoin ransom equivalent to about US$17,000 to hackers who used malware to hold its computer system hostage.
WHAT WE DON'T KNOW
- Who is behind the attack?
While the Shadow Broker hackers released one of the tools used in the attack, it is not clear who orchestrated Friday's attacks (May 12). It is also not clear who the Shadow Broker hackers are. Initially, an insider at the NSA or the CIA was suspected of having leaked the agency's hacking tools, but the hackings continued after an NSA contractor was arrested.
Security experts have said that the timing of the hackers' data dumps often align with Russian political interests. For instance, one of the latest Shadow Broker dumps occurred after the US bombed Syria. Hackers cited the bombing as part of the impetus for their latest leak.
- Has anyone paid the ransom?
Security experts said those who had already fallen victim to ransomware on Friday may have little recourse. Jason Rebholz, a senior director at Crypsis Group, which specialises in ransomware, said victims could try to search the web for a decryption service, but chances are that in a sophisticated attack like this one, cybercriminals had already taken steps to immunise their encryption from such services.
- Has anyone been harmed?
Emergency rooms, doctors' offices and ambulances were disrupted in Britain and communications were affected in other countries. It is still unknown if anyone suffered further injury or died because of the disruption.