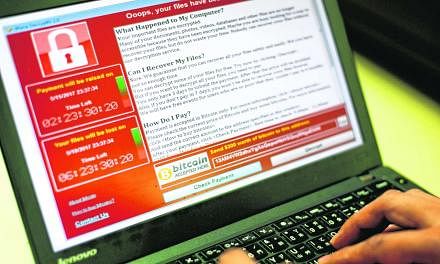
LONDON • Cybercrimes like the global ransomware attack that began last Friday are in a way an updated version of ancient criminal methods.
And in the search for the criminals, investigators are following much the same process that detectives have used for decades: Secure the crime scene, collect forensic evidence and try to trace the clues back to the perpetrator.
But for all of their similarities to traditional crimes, cyber attacks have major digital twists that can make them much harder to solve and can greatly magnify the damage.
Such a large, complex and global crime outbreak means any hope of a successful investigation will require close teamwork among international law enforcement agencies - such as the Federal Bureau of Investigation (FBI), Scotland Yard and security officials in China and Russia - often wary of sharing information with one another.
"With cybercrime, you can operate globally without ever having to leave your home," said Mr Brian Lord, a former deputy director for intelligence and cyber operations at Government Communications Headquarters, Britain's equivalent of the US National Security Agency.
"Catching who did this is going to be very hard, and will require a level of international cooperation from law enforcement that does not come naturally."
As with a crime scene, the first step with a cyber investigation is to make sure the criminal is no longer hiding, about to pounce again.
"Before we get into who did it, we try to figure out if the bad guys still have access," said Ms Theresa Payton, a former White House chief information officer and founder of cyber-security firm Fortalice. "How do we cordon them off to mitigate further damage?"
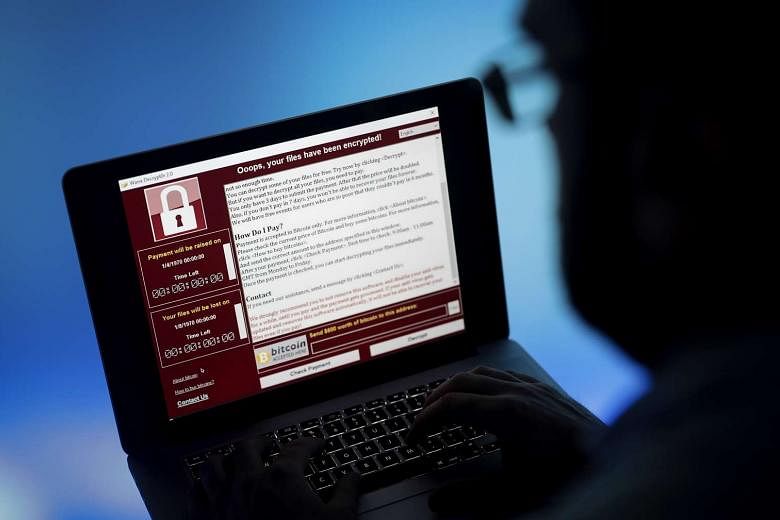
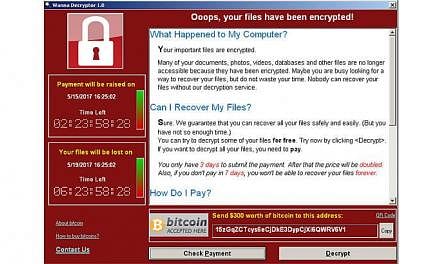
Investigators will examine the affected server, online software caches and e-mails to identify any malware that might not have been activated yet. In the case of the ransomware unleashed last Friday and known as WannaCry, Wcry or Wanna Decryptor, it was quickly determined that updating Windows software with the latest security patch was enough to inoculate computers that had not been infected.
Then the forensic work begins, with agents looking for digital fingerprints.
Because of the highly technical nature of these investigations, private data security teams can be expected to help in the search. That includes working with law enforcement to uncover clues left behind by the attackers, as well as tracking the virus and its effects separately to protect their corporate clients.
In the WannaCry case, investigators will check whether the e-mail address that the malware came from is linked to social media accounts, past cybercrimes or other locations on the Web. They will study the domain name it is linked to. And they will look for patterns to try to connect one crime to others.
Success often depends on whether law enforcement can tie small details, including potential mistakes or a style in the programming code, back to the criminals.
Ultimately, in the world of computers, as in the physical world, investigators rely on criminals to make a mistake. As Mr Adam Malone, a former FBI cyber agent, put it: "A lot of times, we catch bad guys because they get sloppy."
NYTIMES